Unfortunately, No business, organization, or individual is immune to cybercrime. Every employee of an organization, from the CEO on down, is responsible for understanding basic cyber hygiene steps to protect themselves.
In an interview with the Washington Post, Director of the United States Cybersecurity and Infrastructure Security Agency (CISA), Jen Easterly, discussed several recent high-profile cybersecurity news items. Easterly’s statements reveal that ransomware is not showing any signs of slowing down; it remains a serious threat to national security. Below, we will explore the importance of four cybersecurity measures recommended by CISA.
CISA Recommends: Culture of Cybersecurity Awareness
Think before you click! Cybersecurity is a team sport and always has to be a team sport. Automated tools and IT personnel can take measures to scan all emails and maintain endpoint detection software, but a culture of awareness at every level of your organization is your best defense against phishing attacks. If everyone is responsible for understanding basic cybersecurity hygiene, business leaders can help by fostering a culture of cybersecurity awareness at all levels of the company.

Employee security awareness training is a great starting point, with an emphasis on how to spot a phishing attempt. Interestingly, Terranova reports that 20% of employees will click on links from phishing emails, and of that 20%, a whopping 68% will actually provide their credentials when prompted, which is frightening considering it only takes ONE instance of bad judgment to compromise an entire system. Awareness is key to impeding phishing emails, which can potentially expose your organization to destructive malware or expose sensitive credentials, which are the easiest and quickest type of data to compromise.
During your annual or semi-annual company-wide meetings, include cyber-threat discussions in your agenda. Ensure all employees know and understand they are the last line of defense against data breaches and attacks on the company. Some executives also create a culture where their employees know that their first role in the company is Security, and their secondary role is HR, Sales, Accounts Payable, etc.
CISA Recommends: Password Manager
Password management and Privileged Account Management (PAM) play a vital role in thwarting  data breaches. PAM not only acts as a vault to ensure credential complexity and security but can also be configured to do things like logging ALL authentication activity and keep a lookout for strange patterns in user and system activity.
data breaches. PAM not only acts as a vault to ensure credential complexity and security but can also be configured to do things like logging ALL authentication activity and keep a lookout for strange patterns in user and system activity.
Password managers can also improve containment and recovery efforts in the event a breach does occur, allowing you to reset all passwords in the system automatically.
Lastpass, Dashlane, and 1Password are reputable providers
CISA Recommends: Software Updates
Why are software updates important? Security updates protect your organization from data breaches. We are all probably guilty of hitting that “Remind Me Later” button when our phones suggest a software update. However, delaying or ignoring software updates in your business environment can present a huge threat to cybersecurity. Software updates do more than give you access to enhancements and new features. They also address bugs and patch known security flaws, many of which go unnoticed by the average user. Bugs and security flaws are unavoidable with any product, so by ignoring software updates, you are inevitably exposing yourself to vulnerabilities.
In addition to staying on top of software updates, it’s important to remain aware of downloading fraudulent software updates and learn how to identify them. You should only install updates right from the manufacturer’s website.
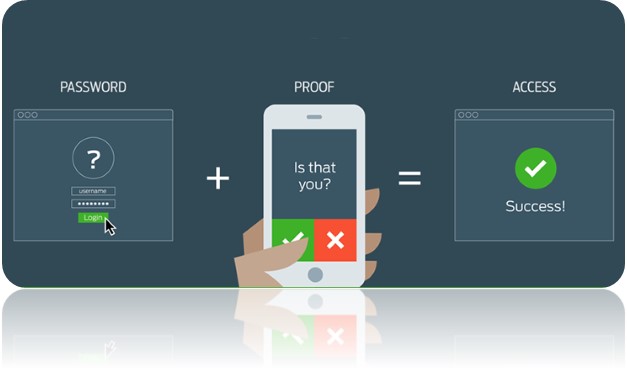
CISA Recommends: Multi-Factor Authentication (MFA)
In addition to password complexity and management, multi-factor authentication is now a staple of cybersecurity best practices. It adds another level of security to your credential management plans. CISA recommends MFA “particularly for webmail, virtual private networks, and accounts that access critical systems.” Remote Desktop Services need more protection now than ever, and for business users, MFA is an incredibly efficient way to add another layer of protection even if the user’s credentials have been compromised.
Summary
According to the CISA, the most common strategies attackers use to deploy ransomware attacks are software vulnerabilities, RDP attacks, and email phishing campaigns.
As your MSP, ICS is involved with addressing cyber risk for many SMBs in the manufacturing, healthcare, and public-sector industries, among others. We have also seen organizations in these sectors span the spectrum of cyber maturity. Your organization‘s cyber security strategy needs to evolve and adapt to new threat environments. These include services that ICS provides such as MFA for Windows Login, Endpoint Detection & Response (EDR), implementation of Cybersecurity Frameworks, Group Policy audits, etc.
Contact ICS today to help your organization prepare and prevent a cyber-catastrophe.
About Us:
- 150+ 5-Star Google Rated IT Firm
- Microsoft Certified Cloud AI Partner
- SOC II Certified Managed Service Provider
- Better Business Bureau A+ Rated






