
With the Russian invasion of Ukraine dominating news headlines, malicious actors are using the issue as an email phishing hook, targeting Microsoft users with warnings of “unusual sign-on activity” from Russia.
The phishing campaign appeared with a subject line and short message supposedly from “The Microsoft account team” that a purported user from Russia/Moscow had recently logged into the targeted user account from a new device. The email message reads:
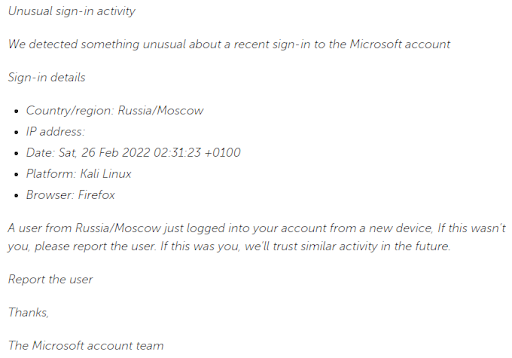
The “Report the User” button opens a new email containing a pre-filled message to be sent to a specific email account which then will ask for login details and possibly payment information.
Victims are at risk of losing control of their accounts to the phishers, and so the best thing to do is not reply and just delete the email.
Taking Advantage of Ukraine Fears
The worsening conflict in Ukraine has everyone on high alert, with the FBI and Cybersecurity and Infrastructure Security Agency (CISA) issuing a joint advisory to help organizations detect and protect their networks from cyberattacks. With the current international crisis in the background of many people’s minds, these types of warnings could affect each individual recipient differently. Depending on personal circumstance and/or what’s happening in the world at any given moment, one person may immediately recognize a phishing email, while another may be curious enough to click and find out more information. Unfortunately, that’s all it may take for some folks to risk losing sole access to their email and all the accounts email is tied to
Phishing Threats Continue
Trying to panic people into hitting a button or clicking a link is an ancient social engineering tactic, but it sticks around because it works. We’ve likely all received a ‘bank details invalid’, or a mysterious ‘payment rejected’ message at one point or another. Phishing attacks continue to emerge around the globe, bringing new challenges to businesses and individuals. Studies indicated that 92% of phishing malware is delivered by email. According to the Verizon 2021 Data Breach Investigations Report (DBIR), phishing is the top data breach tactic, accounting for 36% of reported breaches, up from 25% last year.
To outwit social engineering attacks:
- Slow down and remain in control. If you receive a message that conveys a sense of urgency to act, carefully consider whether you should respond.
- Verify or delete requests to provide financial information or passwords.
- Beware of what you download. Use a reputable web browser and remain conscious of what links you are accessing before clicking on them. Avoid downloading free applications which may possess remote access Trojans that can compromise your device.
- Avoid responding to requests for help or offers to assist from individuals. Browser pop-ups and flashing warning messages try to trick the recipient into calling a phone number or downloading an unapproved application.
As cybercriminals continue to exploit human behavior and take great strides to make their attack vectors appear harmless, it’s important to remain vigilant of how cyber threats continue to evolve
Organization Considerations
Cybersecurity concerns are running high as events unfold in Ukraine and as cyberwarfare, in general, becomes more sophisticated. From business email compromise luring victims into phishing schemes and malware to security and control systems falling prey to bad actors, countless weak spots have become targets for cybercriminals to leverage to access valuable data.
The ICS Security Operations Center managed by Blackpoint Security monitors endpoint activity 24/7 going beyond what antivirus can accomplish or even detect since legitimate and safe tools are often abused by malicious actors. With the optional Blackpoint 365 Defense add-on, an organization’s Microsoft 365 environment can likewise be actively monitored to harden the environment and detect suspicious activities. Please contact ICS for more information about Blackpoint Security 24/7 Operations and Managed Detection and Response capabilities.
About Us:
- 150+ 5-Star Google Rated IT Firm
- Microsoft Certified Cloud AI Partner
- SOC II Certified Managed Service Provider
- Better Business Bureau A+ Rated






