It’s been a boom time for social engineering. Pandemic panic, desperation as income concerns grew, and worry over health and wellness made it easier for criminals to tap into fear.
Social engineering, of course, means attacking the user rather than the computing system itself and trying to extract information or incite an action that will lead to compromise. It's as old as lying, with a new name for the computing age—and that's a perfect metaphor for how social engineering tactics evolve.
Here are some tactics social engineering experts say are on the rise in 2021.
Malicious QR codes
 QR codes—those machine-readable, black-and-white matrix codes arranged in a square—have become an increasingly popular way for companies to engage with consumers and deliver services in the midst of COVID-19. For example, many restaurants have ditched paper menus, and instead allow patrons to scan a QR code with their smartphone. Similarly, many Girl Scouts posted QR codes for no-contact ordering and delivery of cookies this spring.
QR codes—those machine-readable, black-and-white matrix codes arranged in a square—have become an increasingly popular way for companies to engage with consumers and deliver services in the midst of COVID-19. For example, many restaurants have ditched paper menus, and instead allow patrons to scan a QR code with their smartphone. Similarly, many Girl Scouts posted QR codes for no-contact ordering and delivery of cookies this spring.
But many of the websites that QR codes send people to are operated by third-party vendors. When scanned, a malicious QR code can connect phones to a malicious destination—just like clicking on a bad link. People can become conditioned to just assume that the code and website is legit
The ‘delivery’ methods for this social engineering tactic vary. For example, there can be leaflet drops in some neighborhoods with fraudulent codes that promise "Scan this QR code to have a chance of winning an Xbox.” Often the code will lead to a dodgy site that downloads malware to the phone
Browser Notification Hijack
For several years, websites have asked visitors to approve “notifications” from the site. What was once a useful way to engage with readers and keep them up to date is now, of course, also a social engineering tool.
These are called “push notifications” but the problem is that many users blindly click ‘allow’ to allow these notifications. While many users have learned some level of caution with web browsers, the notifications appear more like system messages from the device itself, rather than the browser.
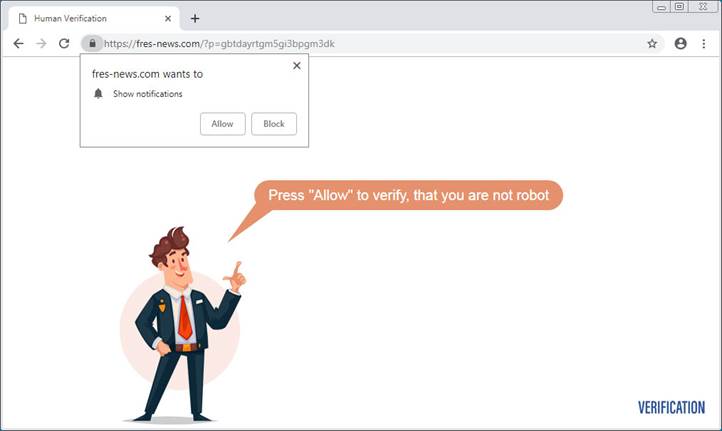
Even for users who don’t blindly say allow, scammers find ways to install their notification scripts. Tactics include disguising subscription consent as another action, like a CAPTCHA, or switching the “accept” and “decline” buttons on subscription alerts mid-action.
Once the crook has a user’s (ill-gotten) consent, they start inundating them with messages—and the messages are usually phishing schemes or scam notifications that contain malware.
Supply chain partner impersonation
It's not easy to defend what you can't see, and you are only as strong as the weakest link. For example, there have been a plethora of targeted emails coming in that look like they are from your trusted partners but are in fact bad actors posing as employees you may know within your network.
In one case, scam gift card offers were presented to one company’s employees- but they wmasked as incentives or thank-yous from the company’s real business partners.
Moreover, there are now long and sophisticated attempts to build trust or relationships with targets. By establishing these trusted relationships, the attackers’ ultimate goal is to make “standard” social engineering tactics more effective, eliciting help in bypassing security controls, or sending along malware that will compromise the target company’s systems.
Text Fraud
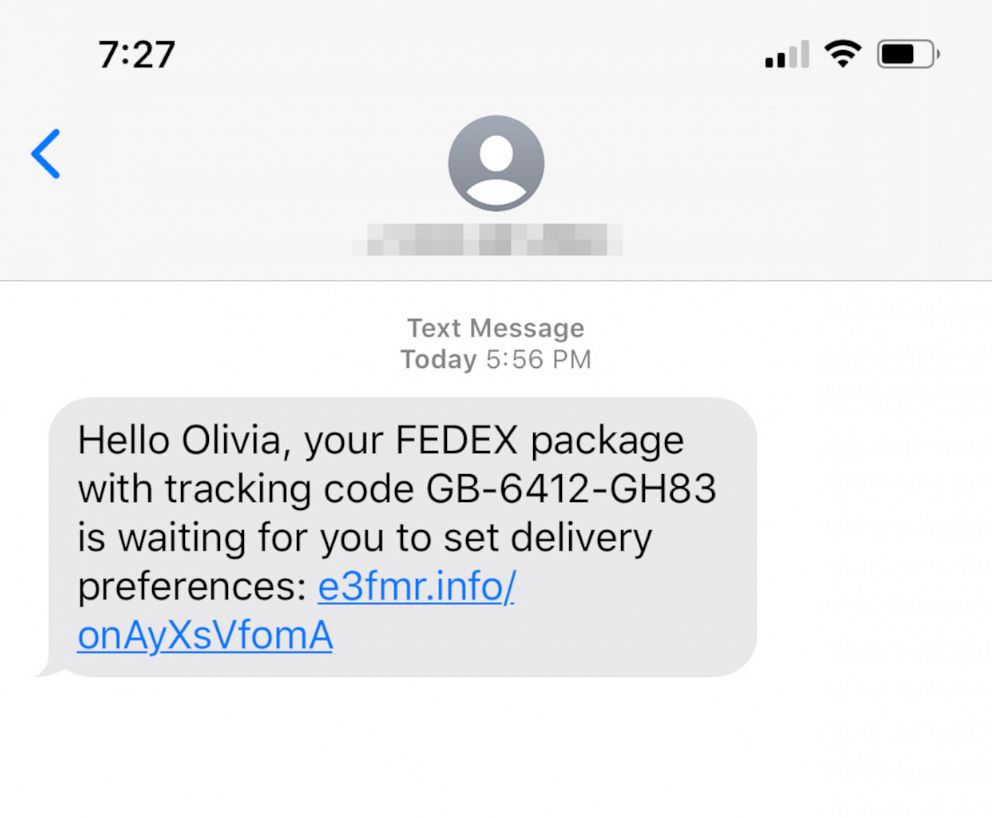 We are becoming a society where a large portion of the population prefers communicating via text messages as opposed to the phone. People are now extremely used to communicating very confidential types of information via text.
We are becoming a society where a large portion of the population prefers communicating via text messages as opposed to the phone. People are now extremely used to communicating very confidential types of information via text.
Because grocery and food delivery has grown in the last year, delivery-related scam texts are up. Other common lures include texts that promise information about COVID stimulus checks that link victims back to a website that looks like the IRS site and asks for sensitive personal information, such as birth date and social security number.
There are text scams in which fraudsters even impersonate the U.S. Department of Health and Human Services and tell victims they must take a "mandatory online COVID test" using a provided link. Then, like other scams, personal information is taken and malware is often loaded onto their device. Depending on where the device is next connected, such as the company wifi, the malware will continuously spread.
Typosquatting or lookalike domains
Typosquatting—or lookalike domains—are often served up in a business email compromise (BEC) attack. Fraudsters impersonate legitimate domains to fool victims into thinking they are in a safe location.
They do this with many tricks, including misspelling the domain (think Gooogle instead of Google) or adding a different top-level domain. Unlike the often sloppy versions from earlier days, today these sites may feature sophisticated designs, carefully detailed mimicry of legitimate sites, and sophisticated functionality.

Social engineering victims are usually tricked into either feeling psychological safety by their choice or into seeking psychological safety in a way that will play into an attacker's hands.
Criminals set these sites not only to deliver malware but also to capture credit card information or other sensitive data through fake login fields or other fake forms.
How Can You Protect Yourself?
There is no antivirus, AI security tool, anti-phishing platform, etc that will protect you from any of the above threats. You are in control of your actions, and who and how you communicate with others.
However, by keeping yourself aware of these tactics, you will help avoid becoming a victim yourself. Now more than ever, be vigilant with your communications.
About Us:
- 150+ 5-Star Google Rated IT Firm
- Microsoft Certified Cloud AI Partner
- SOC II Certified Managed Service Provider
- Better Business Bureau A+ Rated






